
CORPORATE HIJACKING. Security firm Kaspersky Lab just exposed an international cryptocurrency mining ring that is using malware software called PowerGhost to spread across vast corporate networks. The malware is infecting anything from workstations to entire server farms, using corporate hardware to dedicate a portion of the computer’s power to mine a yet-unknown cryptocurrency.
Once a computer is infected, a script downloads the mining tool, which uses the hardware’s processing power to solve complex computational problems. The small amounts of cryptocurrency it mines gets sent back to the attacker’s wallet; the virus, meanwhile, launches a copy of itself to infect other computers connected to the same network.
RANSOM NO MORE. Previous analyses by Kaspersky Lab and security firm Skybox suggested that it is more profitable for cybercriminals — you know, the tinted sunglasses, hoodie-wearing type — to install cryptocurrency mining malware, rather than holding data hostage using ransomware. Browser-based cryptojacking attacks rose 80 percent in 2017, they found.
The difference between these two approaches is fairly simple: mining malware uses processing power of targeted machines — anything from workstations, servers, to even point-of-sales terminals, and people’s smartphones — to mine for obscure cryptocurrencies; ransomware simply locks people out of being able to access their data, threatening to bear their data for all to see. Unless of course, they pay a ransom. That’s how last year’s worldwide ransomware attack WannaCry worked.
WORLD DOMINATION. PowerGhost is even harder to notice than other crypto-mining malware. According to Kaspersky Lab, the malware doesn’t even need to use any files at all, making itself even more invisible to anti-malware and -virus software. Rather than moving files onto the targeted machine to start running mining software, PowerGhost runs a script from memory right away, and bam, it starts mining.
This malware used corporate networks to spread across the entire globe as Kaspersky Lab’s handy map shows:
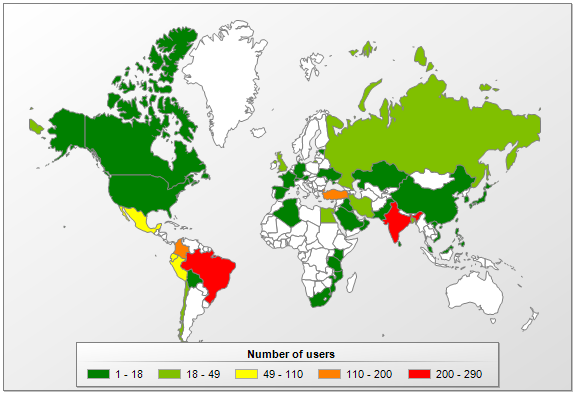
The intent is simple: the more infected computers, the more processing power available to mine more cryptocurrency. The more crypto, the bigger the reward. And as it turns out, targeting corporate networks is an extremely effective way to do just that.
Unfortunately, it’s not always easy to fend off “cryptojacking” malware. Malware communicates with servers in a way very similar to conventional, unsuspicious network communication. And on a big corporate scale, a lot of data could end up hiding the mining software quite well.
If your computer in infected with PowerGhost, installing software updates and patches to avoid being vulnerable to exploits will fix it. But this is surely not the last cryptomining malware we’ll see.
“The miner we examined indicates that targeting consumers is not enough for cybercriminals anymore – threat actors are now turning their attention to enterprises too. Cryptocurrency mining is set to become a huge threat to the business community,” principal security researcher David Emm tells ZDNet.
Translation: cryptomining malware has the potential to turn into a huge headache for everyone.
More about cryptomining: Crypto Mining for Charity: Your Processing Power Could Save the World