
DDoS and DNS
Yesterday was a particularly tough day to enjoy internet browsing. A huge online disruption bothered users of popular sites like Netflix, Twitter, Spotify, Reddit, PayPal, and Pinterest. Even news outlets weren’t exempt, with the New York Times, the Wall Street Journal, the Guardian, and even WIRED experiencing the same disruption.
So what happened?
It was a distributed denial of service (DDoS) attack targeting Dyn, one of the big internet infrastructure companies that run the web’s domain name system (DNS). The first bout of attacks began at around 7 am ET and lasted for two hours. A second wave hit around noon and a third round began at 4 pm ET.
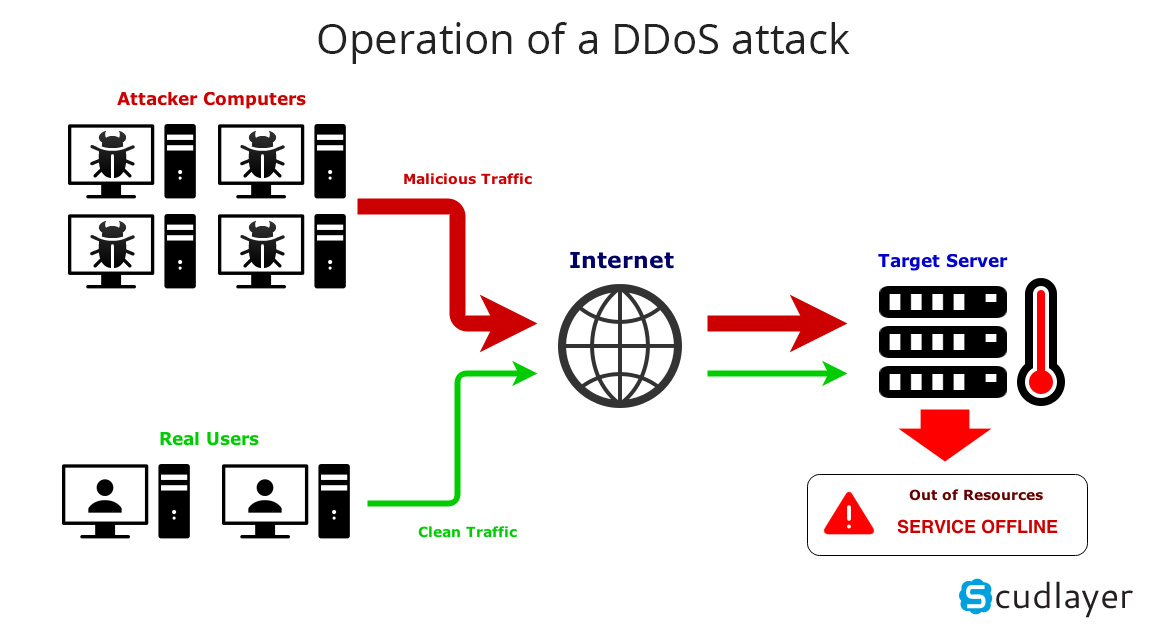
The attacks disrupted traffic to Dyn’s internet directory servers, initially affecting mostly the East Coast and later on spread to the Western Seabord, as well. Dyn servers were flooded with malicious requests from millions of IP addresses, causing the system to halt — like if a human was asked too many questions without enough time to respond. It’s a “very sophisticated and complex attack,” says the New Hampshire-based company. The attacks were also felt on a mitigated scale in Asia.
A DDoS attack is a coordinated hack done through multiple computers serving as bots. The computers themselves do not initiate the attacks. Instead, these have been compromised by malware and serve as part of a network of bots that can deliver DDoS attacks. Friday’s attacks seem to have been made with tens of millions of these compromised machines.
And because Dyn offers DNS services, Friday’s attack was particularly more disruptive. “DNS registrars typically provide authoritative DNS services for thousands or tens of thousands of domain names, and so if there is a service-impacting event the collateral damage footprint can be very large,” Roland Dobbins, a principal engineer at Arbor Networks, explains.
Dyn reports it has resolved the problem by 6:17 pm ET (Friday).
Cybersecurity
“This attack highlights how critical DNS is to maintaining a stable and secure internet presence,” NSFOCUS VP of technology, Richard Meeus, wrote in an email. It also highlights how fragile and vulnerable the internet remains to be.
The Guardian confirms that the Department of Homeland Security has already begun investigations. “The fact that this [caused] Dyn so many problems is pretty good evidence that this [was] an extremely large attack,” Cloudfare CEO Matthew Prince said. “There’s nothing really new about [this type of DDoS attack], he added.

A DDoS attack is not the worst form of hacking out there, but it can certainly be disruptive in a modern world that relies heavily on networking systems. This puts a great deal of pressure for us to develop better cybersecurity measures and defensive measures against similar or worse forms of internet attacks in the future.